Port Authority v2.2.0

Code
This addon is free and open-source software (FOSS) all code can be found here: https://github.com/ACK-J/Port_Authority
Please report your bugs or feature requests in a GitHub issue instead of in a review.
Test if it works!
https://github.com/ACK-J/Port_Authority/blob/main/TestPortScans.html
What does this addon do?
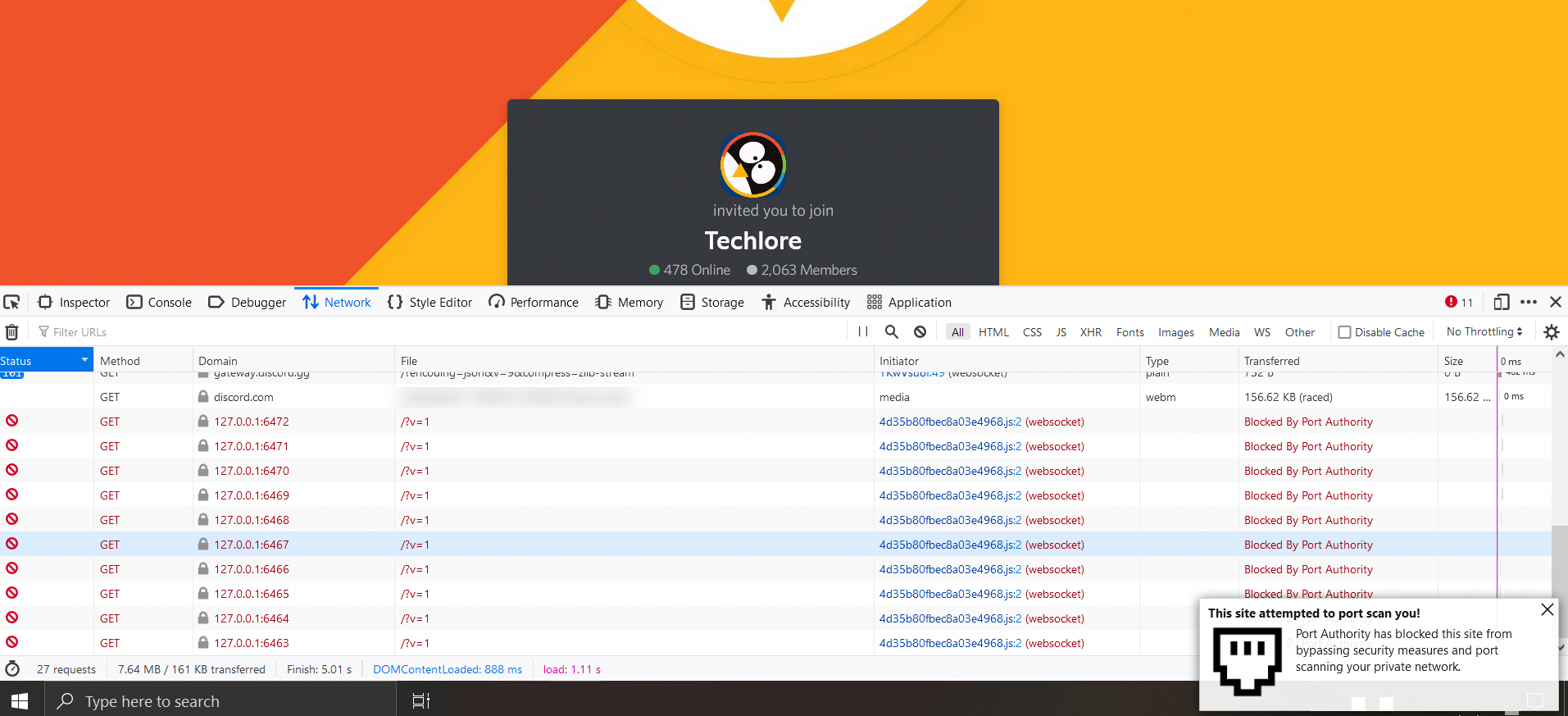
1. Blocks all possible types of port scanning (HTTP/HTTPS/WS/WSS/FTP/FTPS)
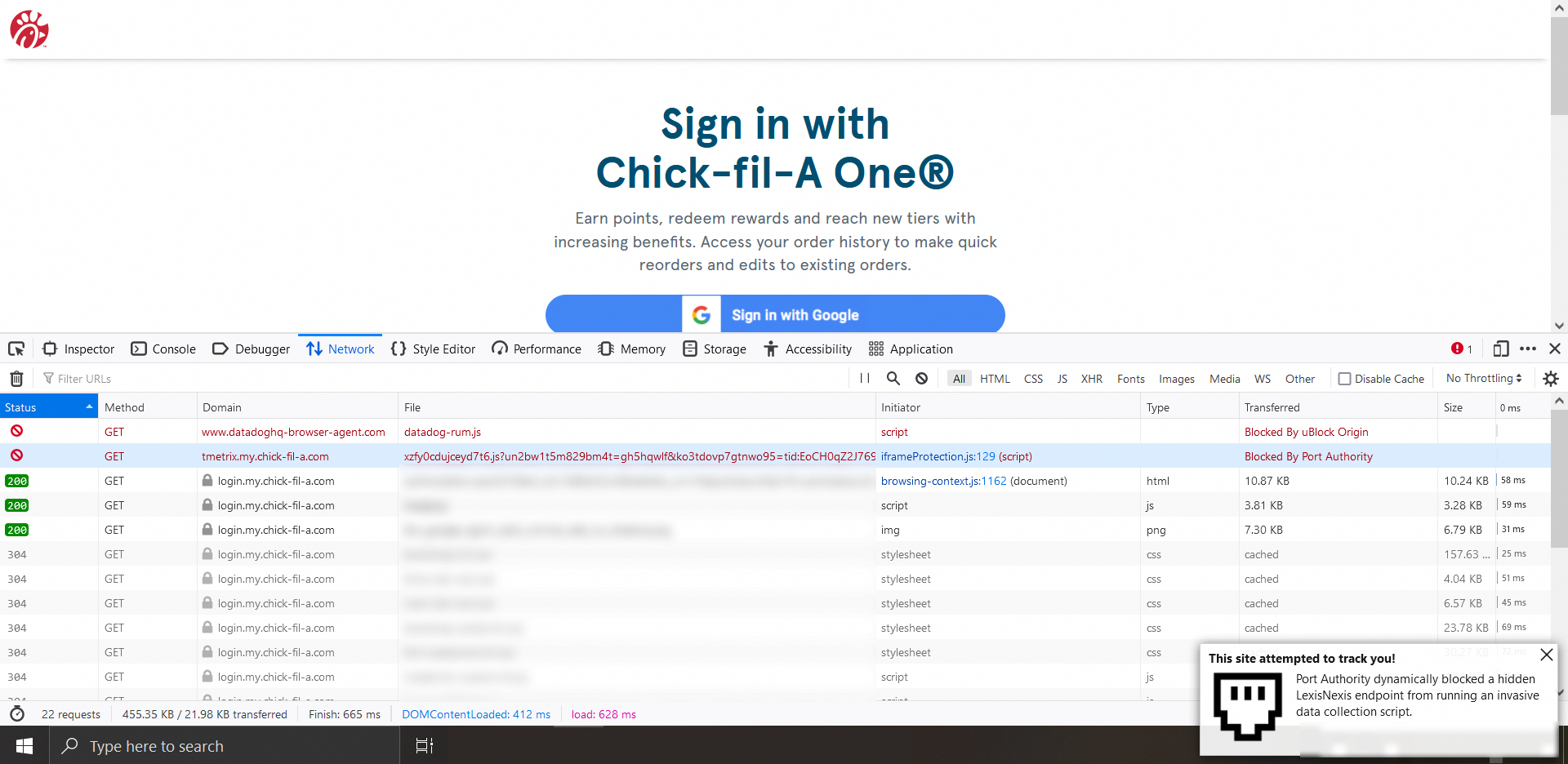
2. Dynamically blocks the LexisNexis ThreatMetrix tracking script.
3. Easily auditable, with the core functionality being about 200 lines of commented code.
4. Sends an optional browser notification when one of the above scenarios are blocked.
5. Provides an optional whitelist to prevent portscans and tracking scripts from being blocked on trusted domains.
6. This addon doesn't store/transmit any data or metadata about you or your requests... because ya know privacy
Donations
Monero Address: 89jYJvX3CaFNv1T6mhg69wK5dMQJSF3aG2AYRNU1ZSo6WbccGtJN7TNMAf39vrmKNR6zXUKxJVABggR4a8cZDGST11Q4yS8
Regex Explanation
Explanation of the regex used to determine local addresses
Explanation of the regex which is used to match the protocol
Test HTTP / HTTPS Portscanning
Site where you can test if HTTP port scanning works: https://defuse.ca/in-browser-port-scanning.htm
Site where you can test if HTTP port scanning works: https://inteltechniques.com/logger/
Site where you can test if HTTP port scanning works: https://ports.sh/
Site where you can test if HTTP port scanning works (Output gives false positives): http://samy.pl/webscan/
Click CTRL + Shift + I to see the networking tab where the blocked port scans will be shown.
Test Websocket Portscanning
Site where you can test if WebSocket port scanning works: https://discord.com/invite/32ZNZVN
Blog Post
Click CTRL + Shift + I to see the networking tab where the blocked port scans will be shown.
Sites that port scan you or otherwise run ThreatMetrix scripts
Permissions Needed
Display notifications to you
This is needed so the addon can alert you when a malicious scripts is blocked or javascrpt port scanning is blocked.
Access browser tabs
This is needed so the addon can display the proper number of blocked requests on a per-tab basis.
Access your data for all websites
This is needed because the addon needs to check every request your browser makes to determine if it needs to be blocked.
Warning!
- USING SOCKS5 PROXIES WITH THIS ADDON WILL CAUSE DNS LEAKS DUE TO HOW FIREFOX HANDLES CNAME LOOKUPS. FOR MORE INFORMATION SEE HERE https://github.com/ACK-J/Port_Authority/issues/7#issue-925519591
- There is a simple fix for this. Type about:config in your browser, accept the warning, search for network.trr.mode and change it to 3
Why I wrote this addon?
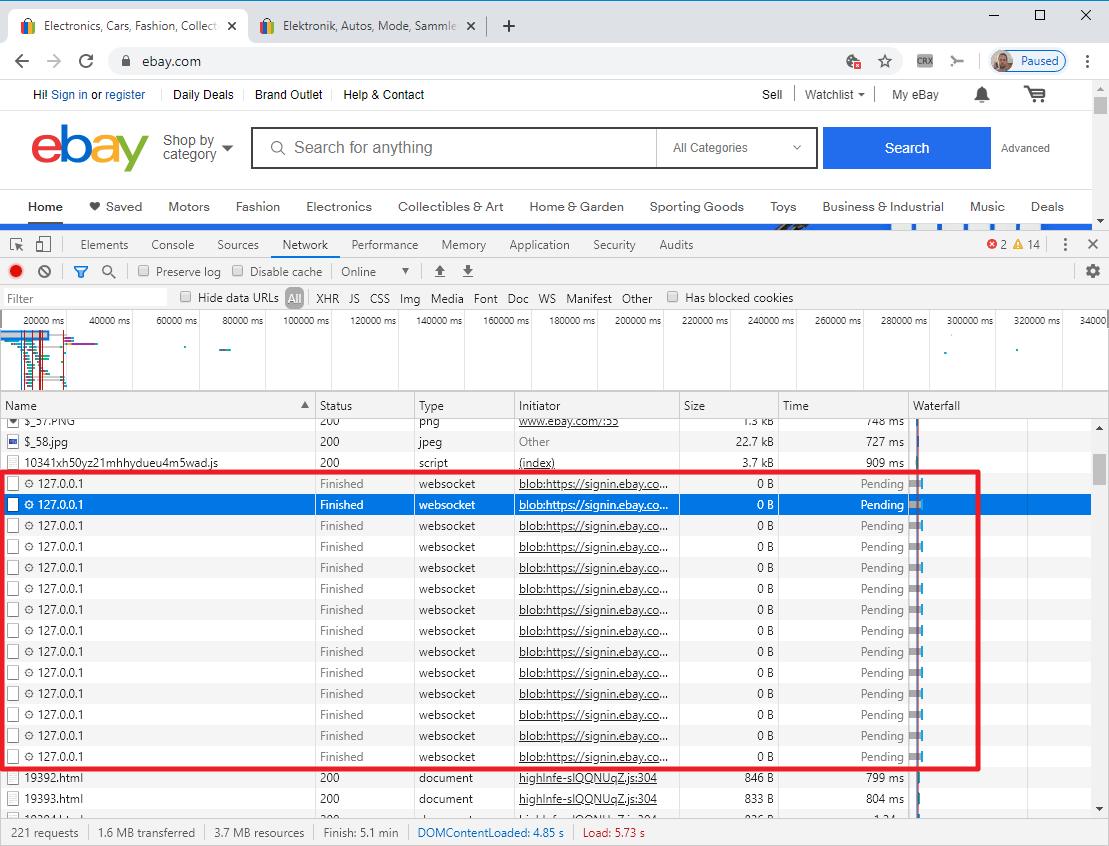
Back in May of 2020 eBay got caught port scanning their customers. I noticed that all of the articles covering this topic mentioned that there was nothing you could do to prevent it... so I wanted to make one. After going down many rabbit holes, I found that this script which was port scanning everyone is, in my opinion, malware.
Here's why I think that:
- The data being exfiled from your computer is encrypted into an image using XOR.
- The domain it reaches out to is made to look legitimate but redirects using a CNAME record to Lexis Nexis' servers.
- It can determine your TrueIP even if you are using a VPN / Proxy. This is likely due to the aggressive fingerprinting. https://web.archive.org/web/20230930123731/https://risk.lexisnexis.com/global/en/products/threatmetrix
- The JavaScript is assembled via string.join (like malware often does) and then executed in a service worker.
- Each time you load the page the JavaScript is re-obfuscated. This makes debugging what they are doing extremely difficult.
- The script collects 416 pieces of personally identifiable information about you and your network. https://gist.github.com/ACK-J/aa8dceb072d31d97a4e7fe0ef389f370
- They talk about trying to bypass adblockers by using encryption in their customer onboarding documentation.
So I developed multiple ways to stop this. The first being the existing functionality built into Port Authority. By default, Port Authority will check the sites that your browser reaches out to and if it redirects to Lexis Nexis' infrastructure, it will be blocked and you will receive a notification. The second is a Python script I wrote which uses Shodan to find all of Lexis Nexis' customer-specific domains on the internet. You can add the output of the script to a blocker such as uBlockOrigin to prevent your computer from connecting to them.
Note: This second method will never include every customer-specific endpoint so you are better off using the dynamic blocking built into Port Authority which WILL block every single customer-specific endpoint Lexis Nexis uses.
Reverse Engineering
Most of these sites are using Lexis Nexis's Threat Metrix scripts, Dan Nemec has a great blog post reverse engineering the script and showing all the invasive data collected https://blog.nem.ec/2020/05/24/ebay-port-scanning/
Zachary Hampton wrote some tools to reverse engineer the ThreatMetrix scripts. Go check it out https://github.com/ZacharyHampton/tmx-solver
* Solver
* Deobfuscator
* Harvester
* Payload Decryption Site
* Network Comparator (compare solver to real implementation)
Tags: ad blocker content blocker privacy security